HIPAA Compliance Checklist for IT

Creating a healthcare app is a challenging but also promising venture. After the corona crisis, telemedicine skyrocketed 2,000%, while telehealth services soared more than 8,300%. Healthcare apps seem to be having their moment and have proven to be immensely helpful.
For those building a healthcare app, HIPAA compliance is of the utmost importance, because PHI (protected health information) should be safe, according to the law. As you probably know, HIPAA is the act that helps to keep confidential health information protected. But how exactly do we adhere to HIPAA regulations? To answer this question, we created this HIPAA compliance checklist.
In the article, we’ll look at HIPAA compliance for IT. By saying “information technology”, we refer to the technological aspect of healthcare app development. We’ll look into tech solutions to make a healthcare tool HIPAA compliant. So if you are planning to build one, you’re on the right track.
We cooked up this HIPAA compliance technology checklist primarily by analyzing the HIPAA Security Rule. We also relied on the Technical Safeguards listed in the official bulletin by the US Department of Health & Human Services. Besides, we shared our own experience, as we’ve built a lot of HIPAA-compliant tools at Riseapps. Hopefully, you’ll find this information helpful and the answers you are looking for.
What is HIPAA Compliance?
For those of you who don’t know much about HIPAA compliance, let’s share with you some basics.
“HIPAA” stands for the Health Insurance Portability and Accountability Act. It was signed into law in 1996 with the main goal is to keep PHI confidential and secure.
To put it shortly, HIPAA compliance involves fulfilling the requirements of HIPAA, as well as the HITECH act (2009) that updated and expanded the HIPAA regulations. This is where any HIPAA compliance software checklist stems from.
Now, what’s PHI? Basically, it’s any health information that can be tied to an individual. Protected health information includes one or more of 18 identifiers like names, dates, account numbers, etc.
Here are some examples of PHI:
- Medical records;
- Insurance information;
- Video, audio chats of patient and physicians (or nurses);
- Patient’s billing information
Speaking of who HIPAA applies to, if you belong to the category of “covered entities” or “business associates,” and deal with PHI, you are required to be HIPAA-compliant. To break it down,
- Covered entities include U.S. health plans, health care providers and health care clearinghouses;
- Business associates refer to any organization or individual who acts as a vendor or subcontractor, having access to PHI. Data processing companies, data transmission providers, data storage firms could be listed as examples.
Obviously, IT companies that provide IT services, e.g. healthcare app development, belong to the second category. A healthcare facility utilizing the work of an IT company or subcontractors must have a “Business Associate” contract in place.
HIPAA violations are investigated by the Office for Civil Rights. In case you are interested, here’s the chart for the last couple of years based on data reported to HHS for breaches affecting hundreds of organizations.
The penalties for violations can be either criminal or financial. So, yes, following the regulations is a must.
To wrap it up, amidst the COVID crisis, the federal government relaxed a number of telehealth rules. However, the restrictions are only temporarily suspended, and HIPAA compliance is still very important.
Privacy Rule and Security Rule
There are two components of HIPAA: privacy and security. These two rules work together to outline what HHS (Health and Human Services) requires as procedures and policies for handling PHI in paper, electronic and other forms.
The Privacy rule sets the standards for access to personal health information (PHI). First enacted in 2002, its goal is to protect the confidentiality of patients and their ePHI. It enables the flow of patient healthcare information when necessary.
The Security rule is more technical, and since our article is for IT, we’ll analyze this exact regulation and its Technical Safeguards. The HIPAA Privacy rule compliance checklist will be left for further discussion. However, in this article, we’ll also touch upon the Physical and Administrative issues of the Security rule.
Now, let’s jump right to the core of the guide. Below, we’ll look at the key security standards (technical safeguards) that serve as a base for our HIPAA network compliance checklist.
Technical Safeguards
Technical safeguards consist of 5 standards, namely
- Access Control
- Audit Controls
- Integrity
- Person or Entity Authentication
- Transmission Security
Below, we’ll briefly explore each of them.
Some of these standards have so-called “implementation specifications” – descriptions indicating how to adhere to these measures. We’ll put attention to them as well.
1. Access Control
The implications of the first standard – Access Control – can be easily guessed from its name. Building a healthcare app, we need to make sure it includes functionality that will allow only authorized users to access ePHI.
According to HIPAA, complying with this standard means using a combination of “access control methods” and “technical controls.”
However, the way to meet this standard is not specified. In other words, the Security Rule does not identify a certain type of access control method or technology to implement. Features and functionality may vary depending on your decision. E.g. you can use any encryption method you consider as best.
By the way, encryption and decryption represent one of the 4 implementation specifications associated with the Access Controls standard. Here’s a full list:
- Unique User Identification
- Emergency Access Procedure
- Automatic Logoff
- Encryption and Decryption
The first two are “required,” the two latter are “addressable.”
Sidenote: “required” means “mandatory”, while “addressable” does not mean optional, but that a specification should be assessed and applied. For more information about “addressable” and “required” look here.
Now, let’s explore the 3rd and 4th implementations of the Access Control standard more closely.
Automatic logoff
Healthcare apps and automatic logoff functionality go hand in hand. Our goal is to architect the tool in a way that after a predetermined period of inactivity it automatically concludes the use of the tool.
Often, apps are created with configuration settings for automatic logoff. For example, your tool can activate an operating system screen saver that is password-protected after a period of system inactivity. Then the information that was displayed on the screen is no longer accessible to unauthorized users.
Needless to say, we’ve implemented this feature in all our healthcare apps. The configuration settings vary in different tools. When we built Genomsoft – a game-changing app for large-scale genomics – we made sure a user is logged off after 15 minutes a device is idle. This serves as an effective way to prevent unauthorized users from accessing PHI.
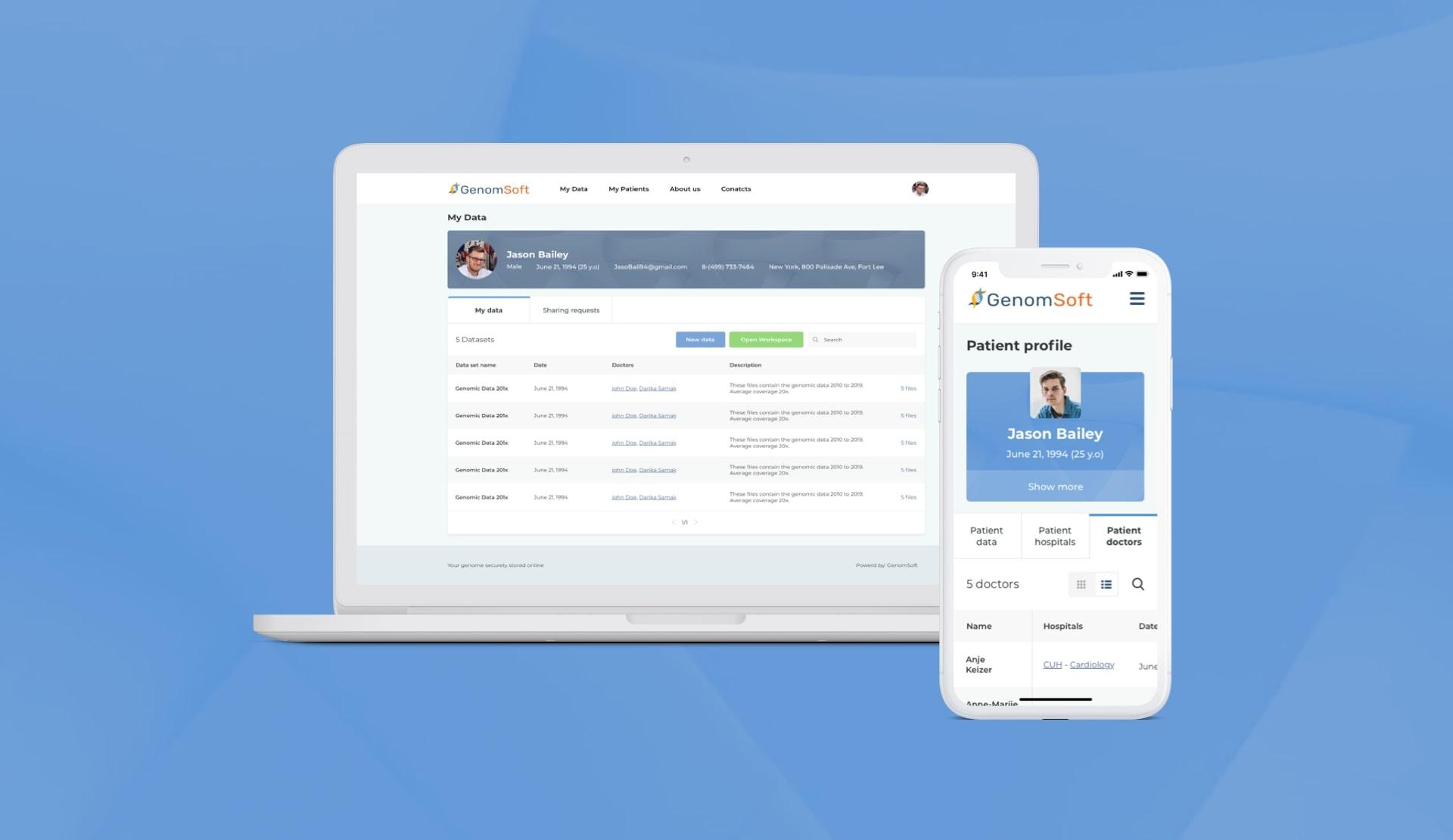
The final set of configuration settings depends on the requirements and may differ greatly. If you need any assistance or expert advice from our experts, let us know.
Encryption and Decryption
This is a final implication of the Access Control standard. In the HIPAA act, we can read about implementing “a mechanism to encrypt and decrypt electronic protected health information.”
As you might know, the basic goal of encryption is to protect ePHI from being accessed and viewed by unauthorized users. The text can be encrypted by means of an algorithm (formula, type of procedure, etc). Then ePHI cannot be read or understood except by people using a system that can decrypt it with a key.
There are many different encryption methods and technologies to protect data – you are free to choose. At Riseapps, when building Kego – a healthcare app for the iOS platform, we used a Keychain framework that allows storing encrypted PHI data.
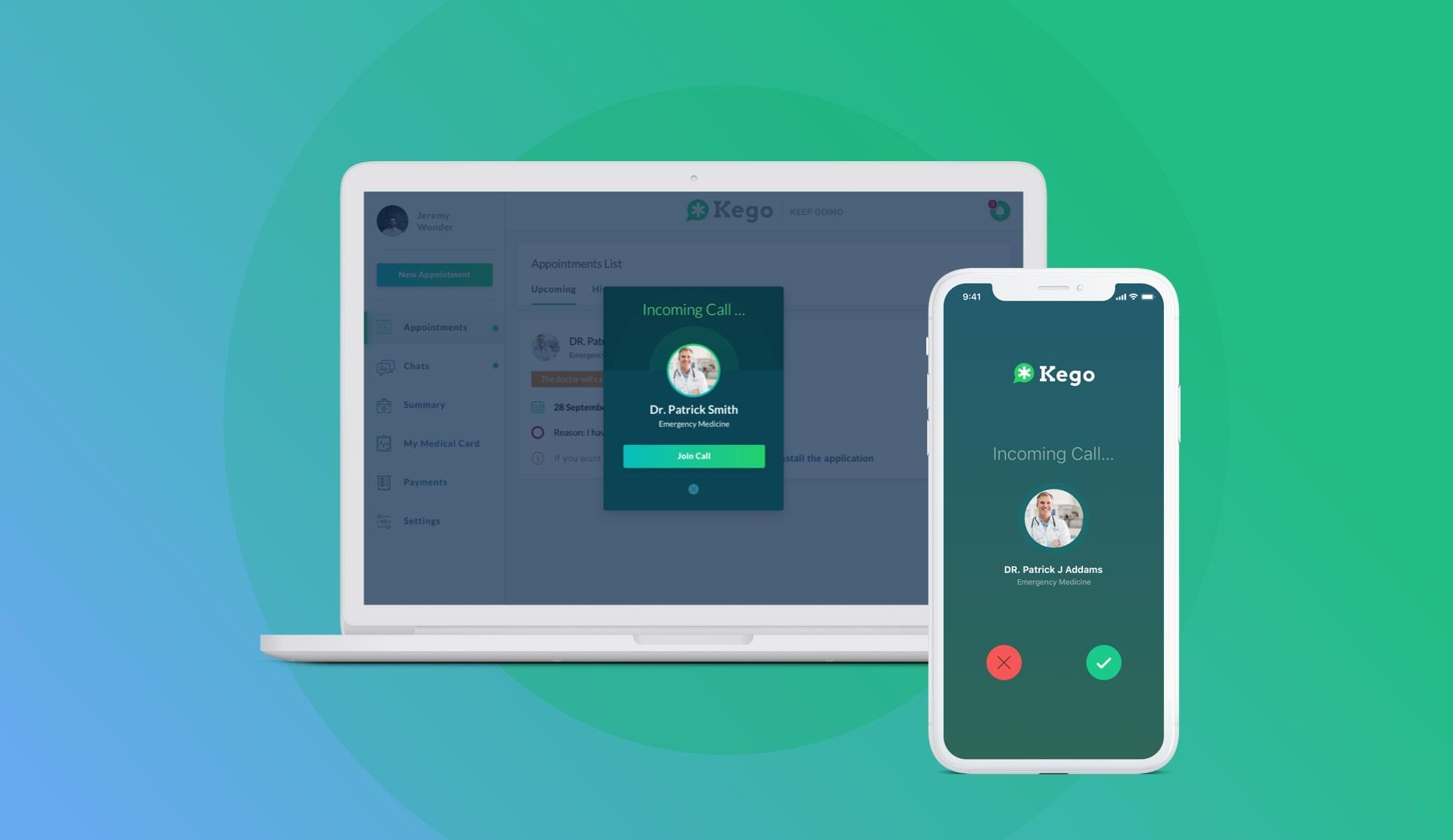
In this section, we are exploring encryption of data stored, but later we’ll get back to the topic when talking about ePHI transmission.
Now, let’s review the HIPAA compliance security checklist in regard to the Access Control standard. Here are 2 questions for the Unique User Identification and Emergency Access Procedure. (We haven’t explored these specifications, but you can learn more about them here.)
- Can the unique user identifier be used to track user activity within information systems that contain ePHI?
- Are there tech solutions in place to provide appropriate access to EPHI in emergency situations?
When it comes to Access Control and Encryption, here are the possible questions to ask:
- Does the tool have an automatic logoff capability?
- What encryption and decryption mechanisms are reasonable and appropriate to implement?
2. Audit Controls
The Audit Controls standard requires “implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems.”
Let’s try to put it more simply. What could help us here is an “audit trail” feature which records who accessed ePHI, what changes were made and when. Then a covered entity can control any modifications suggested to the information.
The Security Rule does not identify data that must be gathered by the audit controls or how often the audit reports should be reviewed. This is what we decide during the exploration, considering risk analysis and organizational factors. If you need help of any kind with this, be sure to let us know.
Speaking of the HIPAA compliance audit checklist, they may include technical infrastructure, hardware and software security capabilities.
This standard has no implementation specifications, so let’s jump right to the key question:
- What will be the audit control capabilities of the information systems with EPHI?
3. Integrity
Simply put, “integrate” means safe. The elaborate description of the “integrity” provided in the Security Rule tells us about “the property that data or information have not been altered or destroyed in an unauthorized manner.” But what does it mean for those building a healthcare app?
Our goal is to ensure that ePHI is protected “from improper alteration or destruction.” It’s not about hacker attacks only. The integrity of data can be compromised by both technical and non-technical ways. For example, data can be altered or destroyed without human intervention, such as by electronic media errors or natural disasters.
Let’s give you an example of how we as app developers can assist covered entities to adhere to this standard.
When we worked on Inteliwound app – a HIPAA compliant wound management software – we needed to take care of the integrity of databases of the tool. Our task was to distribute them geographically. We used Amazon AWS services, which help deploy database servers on both – the west coast and the east coast of the USA.
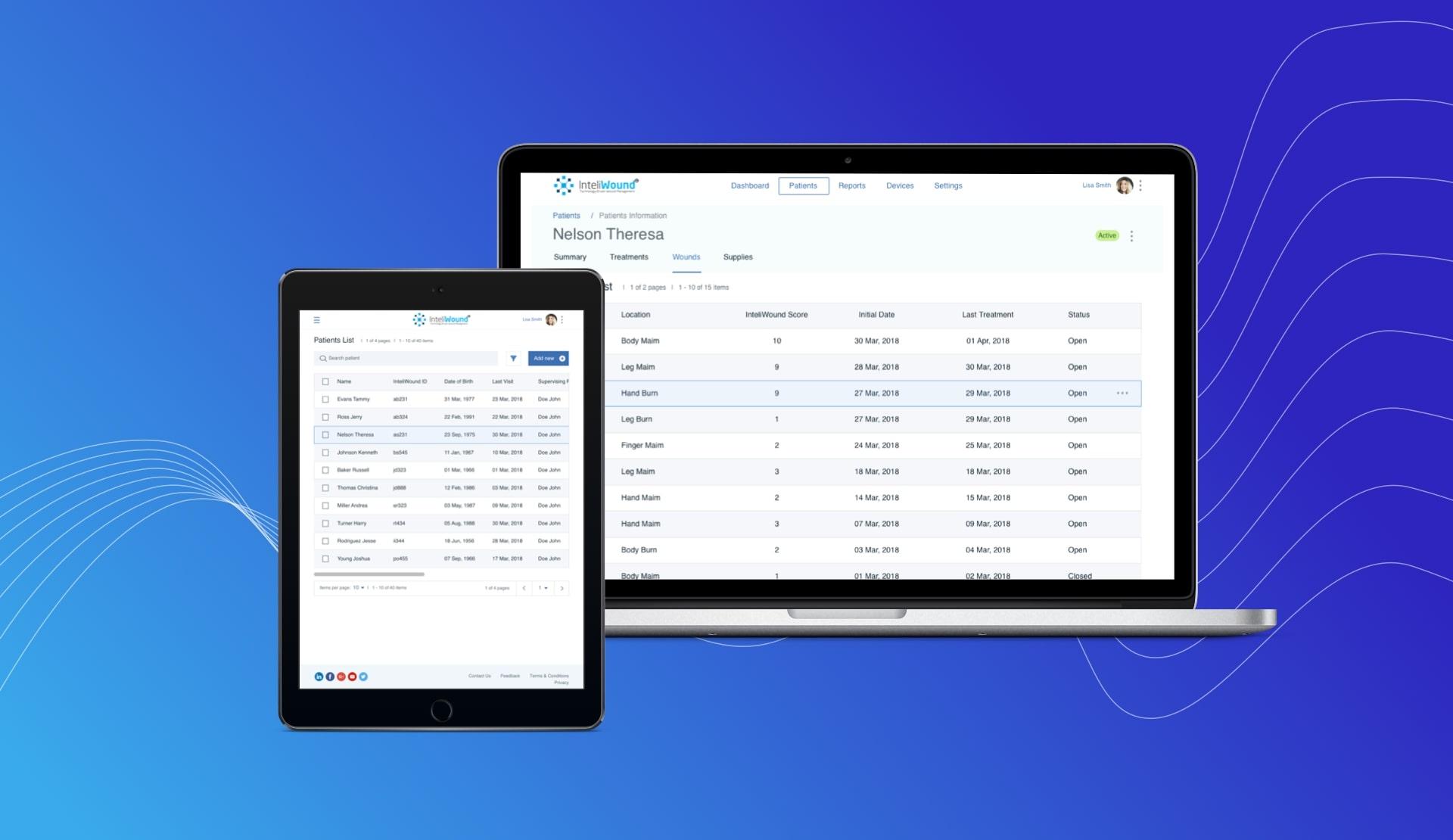
When databases have copies in several places, the information is protected against natural disasters and force majeure.
Getting back to the HIPAA security rule compliance checklist, the key question here will be:
- Are electronic mechanisms to protect the integrity of EPHI currently implemented?
4. Person or Entity Authentication
Here, the goal is to make sure a person or entity seeking access to electronic protected health information is the one claimed. There are a few basic ways to provide proof of identity for authentication.
Authentication ensures that a person is in fact who he (or she) claims to be before being allowed access to EPHI. This is accomplished by providing proof of identity. There are tools simple and complicated. Your tool may require
- Something known only to that individual. It can be a password or PIN. This is a traditional way of authentication, which hasn’t been used much lately.
- Something that individuals possess. It can be a token, smart card, or key. This is one of the most widespread methods of authentication nowadays.
- Something unique to the individual such as a biometric. Examples of biometrics include fingerprints, voice, facial or iris patterns. This is the most advanced method, but the most expensive to implement.
If you are hesitating which type of person or entity authentication is better to implement in your app, let us know. We’ll come up with the most rational and cost-effective solution.
Getting back to our HIPAA computer compliance checklist, the key question here might be
- What types of authentication mechanisms are better to implement?
5. Transmission Security
Finally, there is a standard requiring to implement “measures to guard against unauthorized access” to ePHI transmitted. So here, we are talking about the data not stored but transferred, as in mHealth applications.
Read Also: mHealth App Development: Pitfalls You Should Avoid
The measures depend on the ways of conveying ePHI. If you send it over an electronic open network, it has to be protected, according to the Security Rule.
This is an especially important standard for telemedicine app development tools. If you design a messaging app, you should choose a HIPAA compliant chat API or at least the one that can help you build a HIPAA compliant workflow.
Read Also: HIPAA Compliance and Telehealth: Guidelines 2020
For example, at Riseapps when building Kego, we used Twilio and its SDK for messaging and videoconferencing. (As mentioned, it’s not HIPAA compliant by itself, but we can use it for building a HIPAA compliant app).
The standard has two components that might shed light on how to adhere to it:
- Integrity controls
- Encryption
Let’s have a look at each of them.
Integrity controls
This basically means your ePHI should not be “improperly modified without detection until disposed of.”
A primary method for protecting the integrity of EPHI being transmitted is through the use of network communications protocols. Other methods include data or message authentication codes.
Encryption
Here, we get back to encryption. There are various types of encryption technology. To work properly, both the receiver and the sender should use the same or compatible technology.
Speaking of PHI transmission, at Riseapps, we often use HTTPS – communication protocol encrypting data with SSL/TLS.
Getting back to the HIPAA information technology compliance checklist, here’s the main question:
- What methods of encryption will be used to protect the transmission of EPHI?
Physical and Administrative Safeguards
Since it’s a HIPAA compliance checklist for IT and we address primarily technical safeguards in this guide, we’ll touch Physical and Administrative standards only briefly. However, omitting them in this article would be a mistake.
When experts talk about Physical or Administrative safeguards, the questions usually arise about what covered entities can do to adhere to these standards, e.g. hospitals, doctor’s offices, insurance companies. So it might look as once an app is built, the ball is on the side of a covered entity. However, these rules also apply to IT organizations, managing IT infrastructure and web developers.
E.g. IT companies managing infrastructure shouldn’t allow third parties to access the client’s servers, they are working for. Accordingly, access to the servers should be clearly limited for certain people. Developers who don’t work on the project should have accounts, etc.
The administrative safeguards include
- Security Management Process,
- Assigned Security Responsibility
- Security Incidents Procedures,
- Contingency plan, and more.
You can read more about them here.
Physical safeguards include
- Facility Access Controls
- Workstation Use
- Workstation Security
- Device and Media
- Controls
Feel free to explore more physical safeguards by following this link.
Our experience
Let’s provide you with some more examples of how to meet HIPAA compliance requirements and checking all the boxes when it comes to HIPAA.
Recently, we built CareHalo – a HIPAA-compliant remote patient monitoring tool saving time and resources. It’s a web app for chronic disease management with e-PHI protected according to the highest standards.
Read Also: How to Develop a HIPAA Compliant Website?
Initially, the client took an interest in creating an RMP tool. The app needed to serve as a module in a multifunctional piece of software for chronic disease management. As the tool had to operate with shedloads of vital and sensitive data, it was necessary to develop a steady workflow for doctors and nurses to deal with a multitude of cases.
We created a HIPAA compliant RPM web app – with ‘medical assistant’ and ‘provider’ roles – to take care of patients. We fully met the Access Control standard by building an automatic logoff feature and encrypting all the sensitive data. The audit control feature was implemented as well, so any change in the database is recorded.
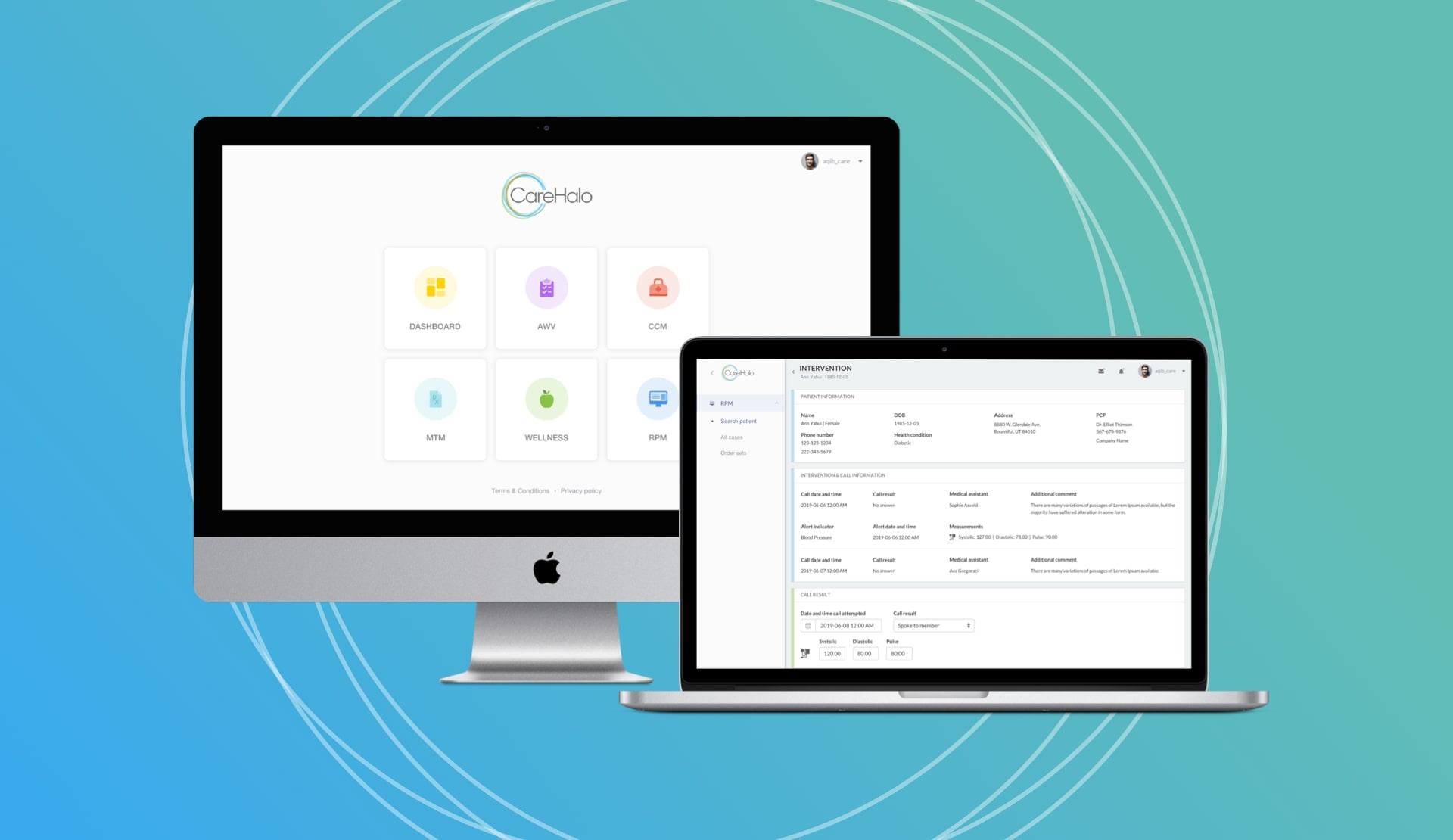
As a result, we built a solid and fast healthcare app. Data collected and managed within the tool can be used to predict and prevent events that’d otherwise require medical intervention. The tool saves money for both – health practitioners and patients, cutting the spendings that come with chronic care and hospital readmission.
Conclusion
Being HIPAA compliant means fulfilling the requirements of HIPAA, as well as the HITECH act (2009).
We’ve explored how those providing IT services can stay HIPAA compliant and assist covered entities in building the HIPAA compliant tools. For this, we’ve looked at the HIPAA Security Rule and reviewed 5 technical standards
- Access Control
- Audit Controls
- Integrity
- Person or Entity authentication
- Transmission Security
Here’s a final HIPAA IT compliance checklist of questions to ask for those providing IT services when building a healthcare tool:
- Can a unique user identifier be used to track the activity of users within information systems that contain EPHI?
- What will be the procedures or policies to provide appropriate access to EPHI in emergency situations?
- Do current information systems have an automatic logoff capability?
- What encryption and decryption mechanisms are reasonable and appropriate to implement?
- What will be the audit control capabilities of information systems with EPHI?
- Are electronic mechanisms to protect the integrity of EPHI currently used?
- What types of authentication mechanisms are better to implement in this particular tool?
In case you feel lost or unsure about the HIPAA compliance checklist for information technology, we are ready to help. If you are going to create a HIPAA-compliant healthcare app, Riseapps is a European software company with deep expertise in building mobile and web apps.
We’ll do our best to come up with the most sensible solution for you, offering high-quality services at a reasonable price. We can build your app from scratch or offer team augmentation services – dedicated experts to assist you with creating your tool
Ping us with a message using the form below to ask any possible questions you have about healthcare app development for your project.
Contact Us






